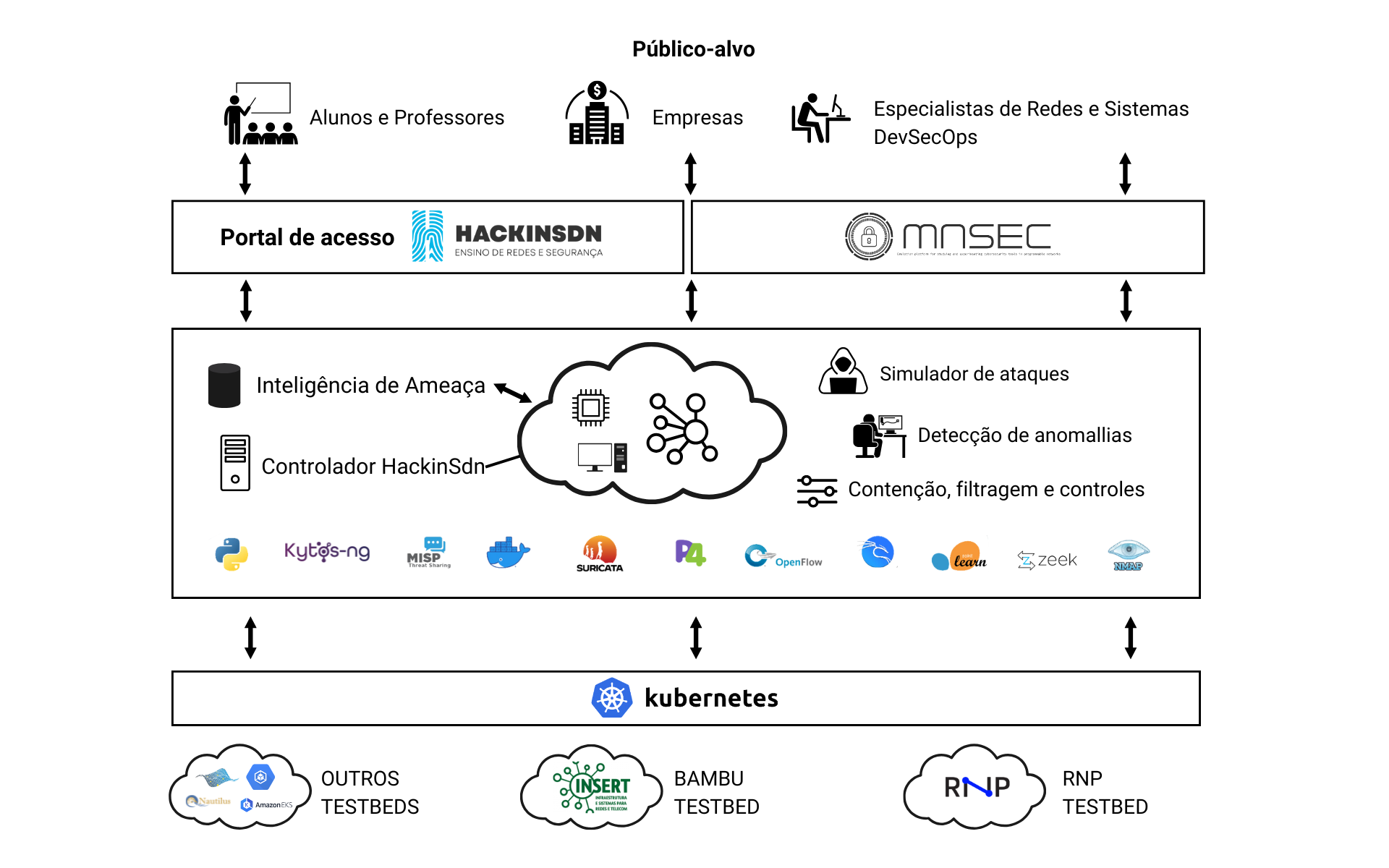
HackInSDN
Aims to strengthen cybersecurity through testbeds, developing tools loaded with scenario elements to understand attacks and block threats. Combined with distributed FPGA infrastructures and a design that provides network flexibility and a robust environment for training.